Conformity
Our security standards.

We take security very seriously. The measures we have implemented—and continually improve—are our way of ensuring the safety of our users, our team, and our services day after day.

All our SSL certificates support 256-bit SSL encryption to guarantee the security of data transmitted with Agendrix.
We make redundant, continuous backups of our user databases, which can be recovered rapidly should problems arise.
We keep the data of our users for as little time as possible, and only when necessary in order to provide our services.
We take advantage of the AWS cloud infrastructure in the ca-central-1 region backed by a 99.99% uptime service level agreement.

Our employees are required to use data only to the extent necessary for the performance of their duties, subject to sanctions.
Our Information Security Incident Management Policy sets out the process to follow in the event of a security incident.
We work exclusively with providers who have implemented information security standards that meet our requirements.
We perform routine background and criminal record checks before approving each hire.
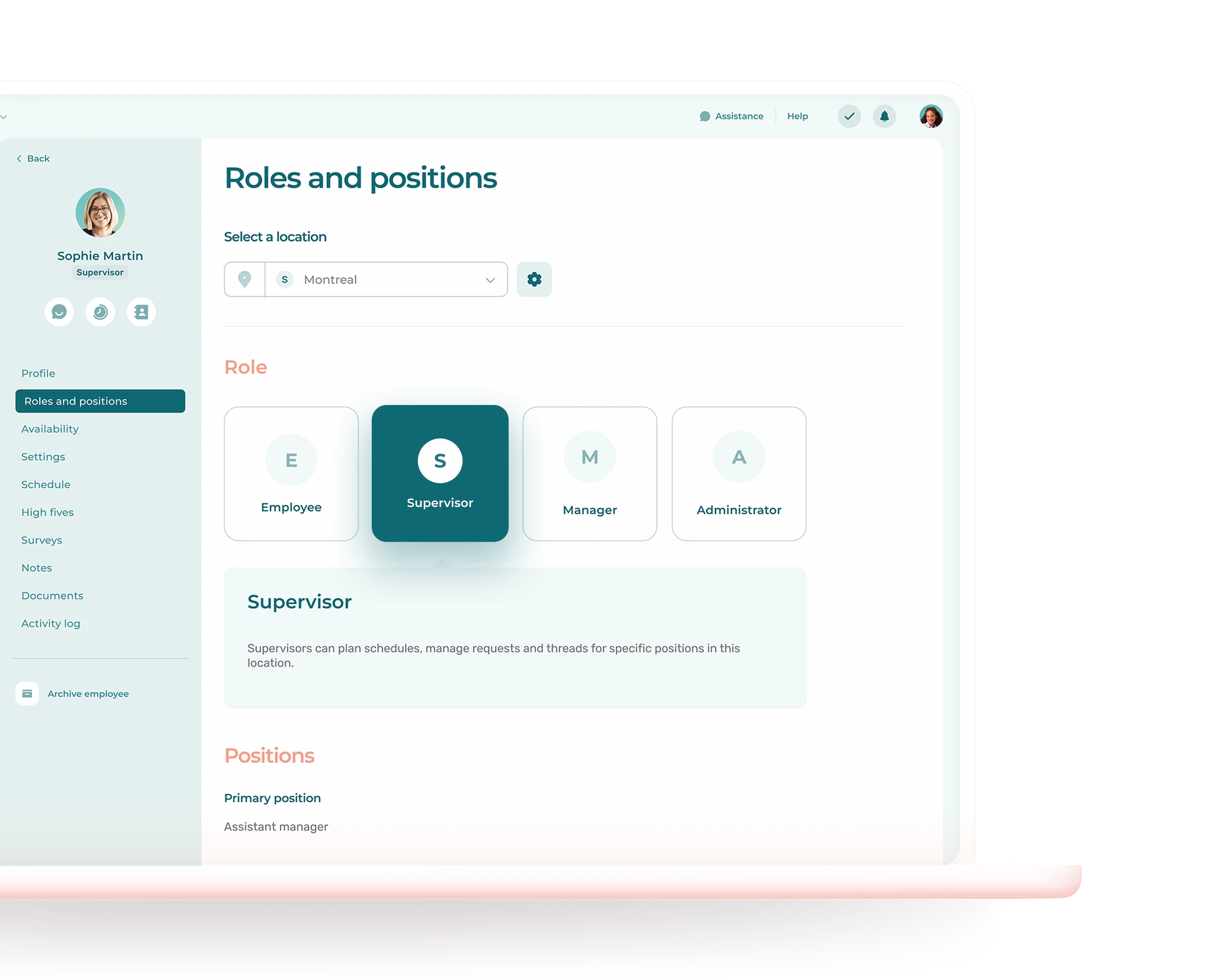
Administrators can enforce the use of multi-factor authentication for every member of their organization.
Administrators can assign a role to each user and set the permissions associated with each role.
Immutable activity logs enable administrators to monitor the actions of every user within their organization.
Administrators have the option of double-encrypting HR data fields they deem sensitive.
Administrators can define security requirements for the passwords of their users, including minimum length and the use of special characters.

